Technology
Let Hackers In: Experts Say Traps Might Be Better Than Walls

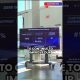
In this Jan. 20, 2015, Kwon Seok-chul, CEO at computer security firm Cuvepia Inc., presents “Kwon-ga,” a real-time monitoring solution that detects hackers during an interview at his office in Seongnam, South Korea. (AP Photo/Ahn Young-joon)
YOUKYUNG LEE, AP Technology Writer
SEOUL, South Korea (AP) — Ever since the Internet blossomed in the 1990s, cybersecurity was built on the idea that computers could be protected by a digital quarantine. Now, as hackers routinely overwhelm such defenses, experts say cybersecurity is beyond due an overhaul.
Their message: Neutralize attackers once they’re inside networks rather than fixating on trying to keep them out.
First they need to convince a conservative business world to gamble on a different approach. And having sold generations of defensive systems that consistently lagged the capabilities of the most advanced hackers, the industry itself must overcome skepticism it’s flogging another illusion of security.
According to U.S. cybersecurity company FireEye, 229 days is the median length of time attackers lurk inside their victim’s computers before being detected or revealing themselves, underscoring the weakness of conventional tools in identifying sophisticated intruders.
The traditional defenses must “have a description of the bad guys before they can help you find them,” said Dave Merkel, chief technology officer at FireEye Inc. “That’s just old and outmoded. And just doesn’t work anymore,” he said.
“There’s no way to guarantee that you never are the victim of cyberattack.”
Merkel said in the worst case he knows of, attackers hid themselves for years.
Experts aren’t recommending organizations stop deploying perimeter defenses such as antivirus software or firewalls that weed out vanilla threats. But they say a strategy that could be likened to laying traps is needed to counter the sophisticated hacks that can cause huge losses.
The weakness of relying on a firewall is that it’s like building a fence around a housing complex but not hiring a guard to patrol the interior streets, said Ed Amoroso, chief security officer at AT&T.
The hackers who targeted Anthem, the second biggest U.S. health insurer, and accessed personal information of 80 million customers, may have been inside its system for more than a month before being detected, according to the company.
In the famous Sony Pictures hack, the attackers who breached the Hollywood studio’s network went unnoticed until computers were paralyzed and a mountain of data was dumped on the Internet.
The amount of data copied and removed from Sony’s systems should have set off internal alarms long before Sony workers found their PCs taken over by malware, said Mike Potts, CEO of Lancope, a network security company based in Alpharetta, Georgia.
The cybersecurity industry characterizes such long-term intrusions as advanced persistent threats or APT. They are often sponsored by states and target valuable commercial and military information.
In South Korea, where government agencies and businesses have come under repeated attacks from hackers traced by Seoul to North Korea, several security firms have jumped on the growing global trend to develop systems that analyze activity to detect potentially suspicious patterns rather than scanning for known threats.
Kwon Seok-chul, CEO at computer security firm Cuvepia Inc., said it has been tough to convince executives that it’s more effective to catch bad guys after they’ve infiltrated a network instead of trying to keep them out, which he believes is impossible anyway.
Kwon said his company’s latest monitoring product keeps a log of all activity, dividing it into authorized users and possible attackers. When certain conditions are met, the program sounds an alarm. A response team, he said, can sit back and watch what hackers copy and respond before damage is done. The security team can cut the hacker’s connection or trick the intruder into stealing empty files.
“Because hackers are in your palm, you can enforce any measures that you want,” said Kwon, member of an advisory board for South Korea’s cyberwarfare command.
In one case, the security team at one of Kwon’s clients “enjoyed” watching for about an hour as a hacker scanned its network and installed tools to unlock passwords and counter antivirus programs.
He said that for skilled hackers, it usually takes about 20 minutes to lay out the initial steps of the attack that allow them to stealthily roam a network. Normally the security team would counterattack within a few minutes after gathering intelligence about the hacker’s tools. But in this case, the hacker was not sophisticated and employed well-known programs mostly made in China.
Eventually, the security team severed the hacker’s connection to the victim’s computer based on the unique ID of the program that Cuvepia’s software showed the hacker was using.
According to FireEye’s Merkel, there is a rise in awareness in the U.S. and growing interest in Asia in modern approaches to information security that include using automated programs to scan for unusual network activity, encryption and segregating sensitive data in special “domains” that require additional credentials to access.
But many companies are in denial about their vulnerability or are reluctant to spend more on cybersecurity, he said.
In the financial industry at least, part of the reason is greater concern with meeting regulatory requirements for security than improving security itself.
When encryption is used, South Korean courts have limited the liability of companies that faced lawsuits from customers over stolen data, said Hwang Weoncheol, a former chief information security officer at a South Korean financial institution. That reinforces the security strategy centered on compliance with regulation, he said.
Protecting high value information often comes with a high price tag.
Installing Cuvepia’s cheapest monitoring product on 1,000 computers for a year costs 450 million won ($410,000). That is many times the cost of installing antivirus software though the cost drops significantly after the first year.
The answer for executives, said Kwon, is to see cybersecurity as an investment not a cost.
___
Youkyung Lee on Twitter: www.twitter.com/YKLeeAP
AP Technology Writer Brandon Bailey in San Francisco contributed.
Copyright 2015 The Associated Press. All rights reserved. This material may not be published, broadcast, rewritten or redistributed.
Community
Attorney General Rob Bonta, Oakland Lawmakers, Introduce Legislation to Protect Youth Online
At a press conference in downtown Oakland on Jan. 29, Attorney General Rob Bonta joined Sen. Nancy Skinner (D-Berkeley) and Assemblymember Buffy Wicks (D-Oakland) to announce two pieces of legislation designed to protect children online. The bills are Senate Bill (SB) 976, the Protecting Youth from Social Media Addiction Act and Assembly Bill (AB) 1949, the California Children’s Data Privacy Act.

By Magaly Muñoz
At a press conference in downtown Oakland on Jan. 29, Attorney General Rob Bonta joined Sen. Nancy Skinner (D-Berkeley) and Assemblymember Buffy Wicks (D-Oakland) to announce two pieces of legislation designed to protect children online.
The bills are Senate Bill (SB) 976, the Protecting Youth from Social Media Addiction Act and Assembly Bill (AB) 1949, the California Children’s Data Privacy Act.
Skinner authored SB 976, which addresses online addiction affecting teenage users, while Wicks’s bill, AB 1949, takes on big tech by proposing data privacy and children rights protections.
“Social media companies unfortunately show us time and time again that they are all too willing to ignore the detriment to our children, the pain to our children, the mental health and physical challenges they face, in order to pursue profits,” Bonta said.
SB 976 would allow parents to control the nature and frequency of the content their under-18-year-old children see on social media. Notifications from social media platforms would also be paused from midnight to 6 am and controls would allow parents to set time limits on their children’s usage based on their discretion.
Skinner stated that the longer that kids are on their phones during the day, the higher the risk for depression, anxiety and other related issues.
The bill would also push to get rid of addictive media that is harmful for young women and girls, specifically image filters that mimic cosmetic plastic surgery.
Bonta and 33 other attorney generals had previously filed a lawsuit against Meta, owner of the popular social media applications Instagram and Facebook. The filing claims that the company purposefully uses algorithmized content that harms younger audiences.
“Social media companies have the ability to protect our kids, they could act, but they do not,” Skinner said.
The Child Data Privacy Act would strengthen existing protections for data privacy under the California Consumer Privacy Act (CCPA). The lawmakers argue that the law does not have effective protection for those under 18 years old.
Wicks stated that the bill would forbid businesses from collecting, using, sharing, or selling personal data of anyone underage unless they receive informed consent, or it becomes necessary for the purpose of the business.
Wicks added that the acts would make it so that a search on the internet like “How do I lose weight?” would not result in dieting pill advertisements targeting youth, which, some experts report, could be harmful to their mental and physical health.
“In a digital age where the vulnerabilities of young users are continually exploited, we cannot afford to let our laws lag behind, our children deserve complete assurance that their online experience will be safeguarded from invasive practices,” Wicks said.
Supporters of the two acts say they have gained bipartisan support issue, but the authors and Bonta expect them to be met with pushback from the affected companies.
#NNPA BlackPress
Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible
Performance & Handling Powered by a robust 5.0 Liter Supercharged 8 Cylinder Gas Engine, the F-Type R75 doesn’t just purr; it roars with a mighty 575 horsepower and 516 lb-ft of torque. Coupled with an 8-speed Automatic Transmission, the car offers an exhilarating drive that is both fast and smooth. The All-Wheel Drive system ensures […]
The post Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible first appeared on BlackPressUSA.

Performance & Handling
Powered by a robust 5.0 Liter Supercharged 8 Cylinder Gas Engine, the F-Type R75 doesn’t just purr; it roars with a mighty 575 horsepower and 516 lb-ft of torque. Coupled with an 8-speed Automatic Transmission, the car offers an exhilarating drive that is both fast and smooth. The All-Wheel Drive system ensures excellent traction and stability, making it a joy to handle in various driving conditions. The Electric Power Assisted Steering and JaguarDrive Control with Selectable Driving Modes add to the car’s agility, providing a driving experience that is as intuitive as it is thrilling. Additionally, the Adaptive Dynamics and Electronic Active Differential with Torque Vectoring by Braking enhance the car’s responsiveness, making every turn a testament to its engineering prowess. Unique to AutoNetwork.com.
with Selectable Driving Modes add to the car’s agility, providing a driving experience that is as intuitive as it is thrilling. Additionally, the Adaptive Dynamics and Electronic Active Differential with Torque Vectoring by Braking enhance the car’s responsiveness, making every turn a testament to its engineering prowess. Unique to AutoNetwork.com.
Like us on and share https://www.facebook.com/autonetwork
#AutoNetwork
#AutoNetworkReports
Subscribe to our channel now for more videos.
Twitter http://www.twitter.com/liveautos
LinkedIn http://www.linkedin.com/in/autonetwork
Coupons Offers and Deals https://www.couponsoffersanddeals.com/
The post Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible first appeared on BlackPressUSA.
#NNPA BlackPress
Elevate Your Ride…
Join us for a virtual car’s best-detailed walkaround of the sleek and stylish 2024 Jaguar F-TYPE AWD convertible. Get an up-close look at the exterior design, interior features, and performance capabilities of this luxury sports car. From its powerful engine to its advanced technology, this video will give you a comprehensive overview of what makes […]
The post Elevate Your Ride… first appeared on BlackPressUSA.

Join us for a virtual car’s best-detailed walkaround of the sleek and stylish 2024 Jaguar F-TYPE AWD convertible. Get an up-close look at the exterior design, interior features, and performance capabilities of this luxury sports car. From its powerful engine to its advanced technology, this video will give you a comprehensive overview of what makes the F-TYPE AWD convertible stand out on the road. Unique to AutoNetwork.com.
Like us on and share https://www.facebook.com/autonetwork
#AutoNetwork
#AutoNetworkReports
Subscribe to our channel now for more videos.
Twitter http://www.twitter.com/liveautos
LinkedIn http://www.linkedin.com/in/autonetwork
Coupons Offers and Deals https://www.couponsoffersanddeals.com/
The post Elevate Your Ride… first appeared on BlackPressUSA.
-

 Activism4 weeks ago
Activism4 weeks agoOakland Post: Week of March 20 – 26, 2024
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoCOMMENTARY: D.C. Crime Bill Fails to Address Root Causes of Violence and Incarceration
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoMayor, City Council President React to May 31 Closing of Birmingham-Southern College
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoFrom Raids to Revelations: The Dark Turn in Sean ‘Diddy’ Combs’ Saga
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoCOMMENTARY: Lady Day and The Lights!
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoBaltimore Key Bridge Catastrophe: A City’s Heartbreak and a Nation’s Alarm
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoBaltimore’s Key Bridge Struck by Ship, Collapses into Water
-

 Activism3 weeks ago
Activism3 weeks agoOakland Post: Week of March 27 – April 2, 2024
Technology
Let Hackers In: Experts Say Traps Might Be Better Than Walls

In this Jan. 20, 2015, Kwon Seok-chul, CEO at computer security firm Cuvepia Inc., presents “Kwon-ga,” a real-time monitoring solution that detects hackers during an interview at his office in Seongnam, South Korea. (AP Photo/Ahn Young-joon)
YOUKYUNG LEE, AP Technology Writer
SEOUL, South Korea (AP) — Ever since the Internet blossomed in the 1990s, cybersecurity was built on the idea that computers could be protected by a digital quarantine. Now, as hackers routinely overwhelm such defenses, experts say cybersecurity is beyond due an overhaul.
Their message: Neutralize attackers once they’re inside networks rather than fixating on trying to keep them out.
First they need to convince a conservative business world to gamble on a different approach. And having sold generations of defensive systems that consistently lagged the capabilities of the most advanced hackers, the industry itself must overcome skepticism it’s flogging another illusion of security.
According to U.S. cybersecurity company FireEye, 229 days is the median length of time attackers lurk inside their victim’s computers before being detected or revealing themselves, underscoring the weakness of conventional tools in identifying sophisticated intruders.
The traditional defenses must “have a description of the bad guys before they can help you find them,” said Dave Merkel, chief technology officer at FireEye Inc. “That’s just old and outmoded. And just doesn’t work anymore,” he said.
“There’s no way to guarantee that you never are the victim of cyberattack.”
Merkel said in the worst case he knows of, attackers hid themselves for years.
Experts aren’t recommending organizations stop deploying perimeter defenses such as antivirus software or firewalls that weed out vanilla threats. But they say a strategy that could be likened to laying traps is needed to counter the sophisticated hacks that can cause huge losses.
The weakness of relying on a firewall is that it’s like building a fence around a housing complex but not hiring a guard to patrol the interior streets, said Ed Amoroso, chief security officer at AT&T.
The hackers who targeted Anthem, the second biggest U.S. health insurer, and accessed personal information of 80 million customers, may have been inside its system for more than a month before being detected, according to the company.
In the famous Sony Pictures hack, the attackers who breached the Hollywood studio’s network went unnoticed until computers were paralyzed and a mountain of data was dumped on the Internet.
The amount of data copied and removed from Sony’s systems should have set off internal alarms long before Sony workers found their PCs taken over by malware, said Mike Potts, CEO of Lancope, a network security company based in Alpharetta, Georgia.
The cybersecurity industry characterizes such long-term intrusions as advanced persistent threats or APT. They are often sponsored by states and target valuable commercial and military information.
In South Korea, where government agencies and businesses have come under repeated attacks from hackers traced by Seoul to North Korea, several security firms have jumped on the growing global trend to develop systems that analyze activity to detect potentially suspicious patterns rather than scanning for known threats.
Kwon Seok-chul, CEO at computer security firm Cuvepia Inc., said it has been tough to convince executives that it’s more effective to catch bad guys after they’ve infiltrated a network instead of trying to keep them out, which he believes is impossible anyway.
Kwon said his company’s latest monitoring product keeps a log of all activity, dividing it into authorized users and possible attackers. When certain conditions are met, the program sounds an alarm. A response team, he said, can sit back and watch what hackers copy and respond before damage is done. The security team can cut the hacker’s connection or trick the intruder into stealing empty files.
“Because hackers are in your palm, you can enforce any measures that you want,” said Kwon, member of an advisory board for South Korea’s cyberwarfare command.
In one case, the security team at one of Kwon’s clients “enjoyed” watching for about an hour as a hacker scanned its network and installed tools to unlock passwords and counter antivirus programs.
He said that for skilled hackers, it usually takes about 20 minutes to lay out the initial steps of the attack that allow them to stealthily roam a network. Normally the security team would counterattack within a few minutes after gathering intelligence about the hacker’s tools. But in this case, the hacker was not sophisticated and employed well-known programs mostly made in China.
Eventually, the security team severed the hacker’s connection to the victim’s computer based on the unique ID of the program that Cuvepia’s software showed the hacker was using.
According to FireEye’s Merkel, there is a rise in awareness in the U.S. and growing interest in Asia in modern approaches to information security that include using automated programs to scan for unusual network activity, encryption and segregating sensitive data in special “domains” that require additional credentials to access.
But many companies are in denial about their vulnerability or are reluctant to spend more on cybersecurity, he said.
In the financial industry at least, part of the reason is greater concern with meeting regulatory requirements for security than improving security itself.
When encryption is used, South Korean courts have limited the liability of companies that faced lawsuits from customers over stolen data, said Hwang Weoncheol, a former chief information security officer at a South Korean financial institution. That reinforces the security strategy centered on compliance with regulation, he said.
Protecting high value information often comes with a high price tag.
Installing Cuvepia’s cheapest monitoring product on 1,000 computers for a year costs 450 million won ($410,000). That is many times the cost of installing antivirus software though the cost drops significantly after the first year.
The answer for executives, said Kwon, is to see cybersecurity as an investment not a cost.
___
Youkyung Lee on Twitter: www.twitter.com/YKLeeAP
AP Technology Writer Brandon Bailey in San Francisco contributed.
Copyright 2015 The Associated Press. All rights reserved. This material may not be published, broadcast, rewritten or redistributed.
Community
Attorney General Rob Bonta, Oakland Lawmakers, Introduce Legislation to Protect Youth Online
At a press conference in downtown Oakland on Jan. 29, Attorney General Rob Bonta joined Sen. Nancy Skinner (D-Berkeley) and Assemblymember Buffy Wicks (D-Oakland) to announce two pieces of legislation designed to protect children online. The bills are Senate Bill (SB) 976, the Protecting Youth from Social Media Addiction Act and Assembly Bill (AB) 1949, the California Children’s Data Privacy Act.

By Magaly Muñoz
At a press conference in downtown Oakland on Jan. 29, Attorney General Rob Bonta joined Sen. Nancy Skinner (D-Berkeley) and Assemblymember Buffy Wicks (D-Oakland) to announce two pieces of legislation designed to protect children online.
The bills are Senate Bill (SB) 976, the Protecting Youth from Social Media Addiction Act and Assembly Bill (AB) 1949, the California Children’s Data Privacy Act.
Skinner authored SB 976, which addresses online addiction affecting teenage users, while Wicks’s bill, AB 1949, takes on big tech by proposing data privacy and children rights protections.
“Social media companies unfortunately show us time and time again that they are all too willing to ignore the detriment to our children, the pain to our children, the mental health and physical challenges they face, in order to pursue profits,” Bonta said.
SB 976 would allow parents to control the nature and frequency of the content their under-18-year-old children see on social media. Notifications from social media platforms would also be paused from midnight to 6 am and controls would allow parents to set time limits on their children’s usage based on their discretion.
Skinner stated that the longer that kids are on their phones during the day, the higher the risk for depression, anxiety and other related issues.
The bill would also push to get rid of addictive media that is harmful for young women and girls, specifically image filters that mimic cosmetic plastic surgery.
Bonta and 33 other attorney generals had previously filed a lawsuit against Meta, owner of the popular social media applications Instagram and Facebook. The filing claims that the company purposefully uses algorithmized content that harms younger audiences.
“Social media companies have the ability to protect our kids, they could act, but they do not,” Skinner said.
The Child Data Privacy Act would strengthen existing protections for data privacy under the California Consumer Privacy Act (CCPA). The lawmakers argue that the law does not have effective protection for those under 18 years old.
Wicks stated that the bill would forbid businesses from collecting, using, sharing, or selling personal data of anyone underage unless they receive informed consent, or it becomes necessary for the purpose of the business.
Wicks added that the acts would make it so that a search on the internet like “How do I lose weight?” would not result in dieting pill advertisements targeting youth, which, some experts report, could be harmful to their mental and physical health.
“In a digital age where the vulnerabilities of young users are continually exploited, we cannot afford to let our laws lag behind, our children deserve complete assurance that their online experience will be safeguarded from invasive practices,” Wicks said.
Supporters of the two acts say they have gained bipartisan support issue, but the authors and Bonta expect them to be met with pushback from the affected companies.
#NNPA BlackPress
Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible
Performance & Handling Powered by a robust 5.0 Liter Supercharged 8 Cylinder Gas Engine, the F-Type R75 doesn’t just purr; it roars with a mighty 575 horsepower and 516 lb-ft of torque. Coupled with an 8-speed Automatic Transmission, the car offers an exhilarating drive that is both fast and smooth. The All-Wheel Drive system ensures […]
The post Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible first appeared on BlackPressUSA.

Performance & Handling
Powered by a robust 5.0 Liter Supercharged 8 Cylinder Gas Engine, the F-Type R75 doesn’t just purr; it roars with a mighty 575 horsepower and 516 lb-ft of torque. Coupled with an 8-speed Automatic Transmission, the car offers an exhilarating drive that is both fast and smooth. The All-Wheel Drive system ensures excellent traction and stability, making it a joy to handle in various driving conditions. The Electric Power Assisted Steering and JaguarDrive Control with Selectable Driving Modes add to the car’s agility, providing a driving experience that is as intuitive as it is thrilling. Additionally, the Adaptive Dynamics and Electronic Active Differential with Torque Vectoring by Braking enhance the car’s responsiveness, making every turn a testament to its engineering prowess. Unique to AutoNetwork.com.
with Selectable Driving Modes add to the car’s agility, providing a driving experience that is as intuitive as it is thrilling. Additionally, the Adaptive Dynamics and Electronic Active Differential with Torque Vectoring by Braking enhance the car’s responsiveness, making every turn a testament to its engineering prowess. Unique to AutoNetwork.com.
Like us on and share https://www.facebook.com/autonetwork
#AutoNetwork
#AutoNetworkReports
Subscribe to our channel now for more videos.
Twitter http://www.twitter.com/liveautos
LinkedIn http://www.linkedin.com/in/autonetwork
Coupons Offers and Deals https://www.couponsoffersanddeals.com/
The post Unleashing the Power_ Discover the The Thrills…F-TYPE Convertible first appeared on BlackPressUSA.
#NNPA BlackPress
Elevate Your Ride…
Join us for a virtual car’s best-detailed walkaround of the sleek and stylish 2024 Jaguar F-TYPE AWD convertible. Get an up-close look at the exterior design, interior features, and performance capabilities of this luxury sports car. From its powerful engine to its advanced technology, this video will give you a comprehensive overview of what makes […]
The post Elevate Your Ride… first appeared on BlackPressUSA.

Join us for a virtual car’s best-detailed walkaround of the sleek and stylish 2024 Jaguar F-TYPE AWD convertible. Get an up-close look at the exterior design, interior features, and performance capabilities of this luxury sports car. From its powerful engine to its advanced technology, this video will give you a comprehensive overview of what makes the F-TYPE AWD convertible stand out on the road. Unique to AutoNetwork.com.
Like us on and share https://www.facebook.com/autonetwork
#AutoNetwork
#AutoNetworkReports
Subscribe to our channel now for more videos.
Twitter http://www.twitter.com/liveautos
LinkedIn http://www.linkedin.com/in/autonetwork
Coupons Offers and Deals https://www.couponsoffersanddeals.com/
The post Elevate Your Ride… first appeared on BlackPressUSA.
-

 Activism4 weeks ago
Activism4 weeks agoOakland Post: Week of March 20 – 26, 2024
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoCOMMENTARY: D.C. Crime Bill Fails to Address Root Causes of Violence and Incarceration
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoMayor, City Council President React to May 31 Closing of Birmingham-Southern College
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoFrom Raids to Revelations: The Dark Turn in Sean ‘Diddy’ Combs’ Saga
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoCOMMENTARY: Lady Day and The Lights!
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoBaltimore Key Bridge Catastrophe: A City’s Heartbreak and a Nation’s Alarm
-

 #NNPA BlackPress3 weeks ago
#NNPA BlackPress3 weeks agoBaltimore’s Key Bridge Struck by Ship, Collapses into Water
-

 Activism3 weeks ago
Activism3 weeks agoOakland Post: Week of March 27 – April 2, 2024



















































Leave a Reply